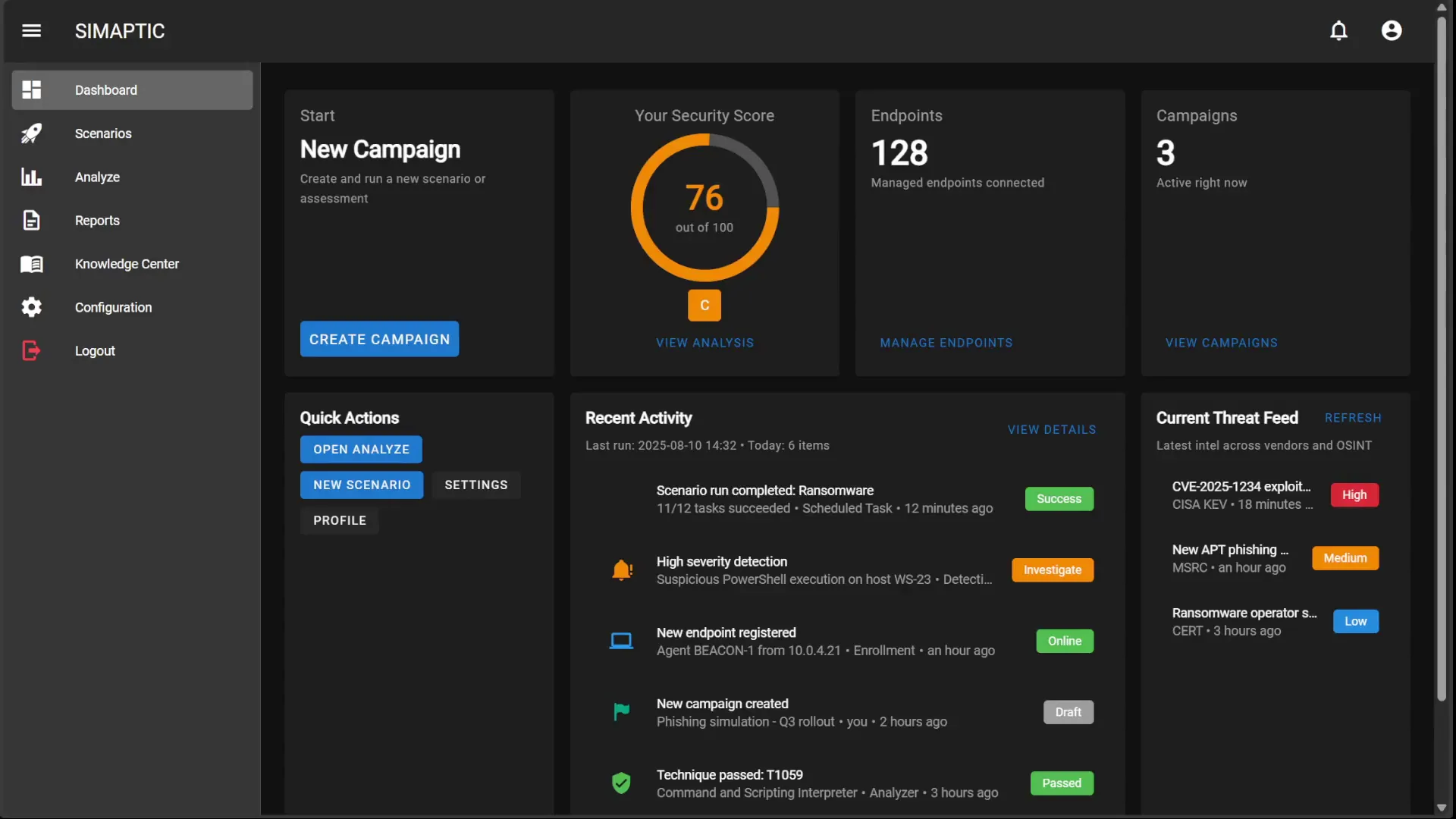
SIMAPTIC Delivers Realistic, Continuous Security Validation
Autonomous Campaign Builder
Our AI designs multi-stage attack scenarios (credential theft, lateral movement, exfiltration) tailored to your environment.
Realistic Emulation
Executes real adversary tools and live C2 in a controlled way, generating genuine IOCs your team can act on.
Continuous & Scalable
Always-on simulations keep pace with change, validating controls 24/7 across on‑prem and cloud.
Build Resilience with AI-Driven Simulations
Introducing SIMAPTIC
Continuous Threat Exposure and Management
SIMAPTIC builds and runs realistic, multi-stage attack campaigns and turns the results into clear, actionable reports. It orchestrates the same tools and techniques real adversaries use across on-premises and cloud environments.
What it does
- Build campaigns: Credential theft, lateral movement, data exfiltration.
- Emulate real tools: Authentic Indicators of Compromise (IOCs) and live C2 traffic.
- Report & recommend: Concise fixes and metrics leaders can use.
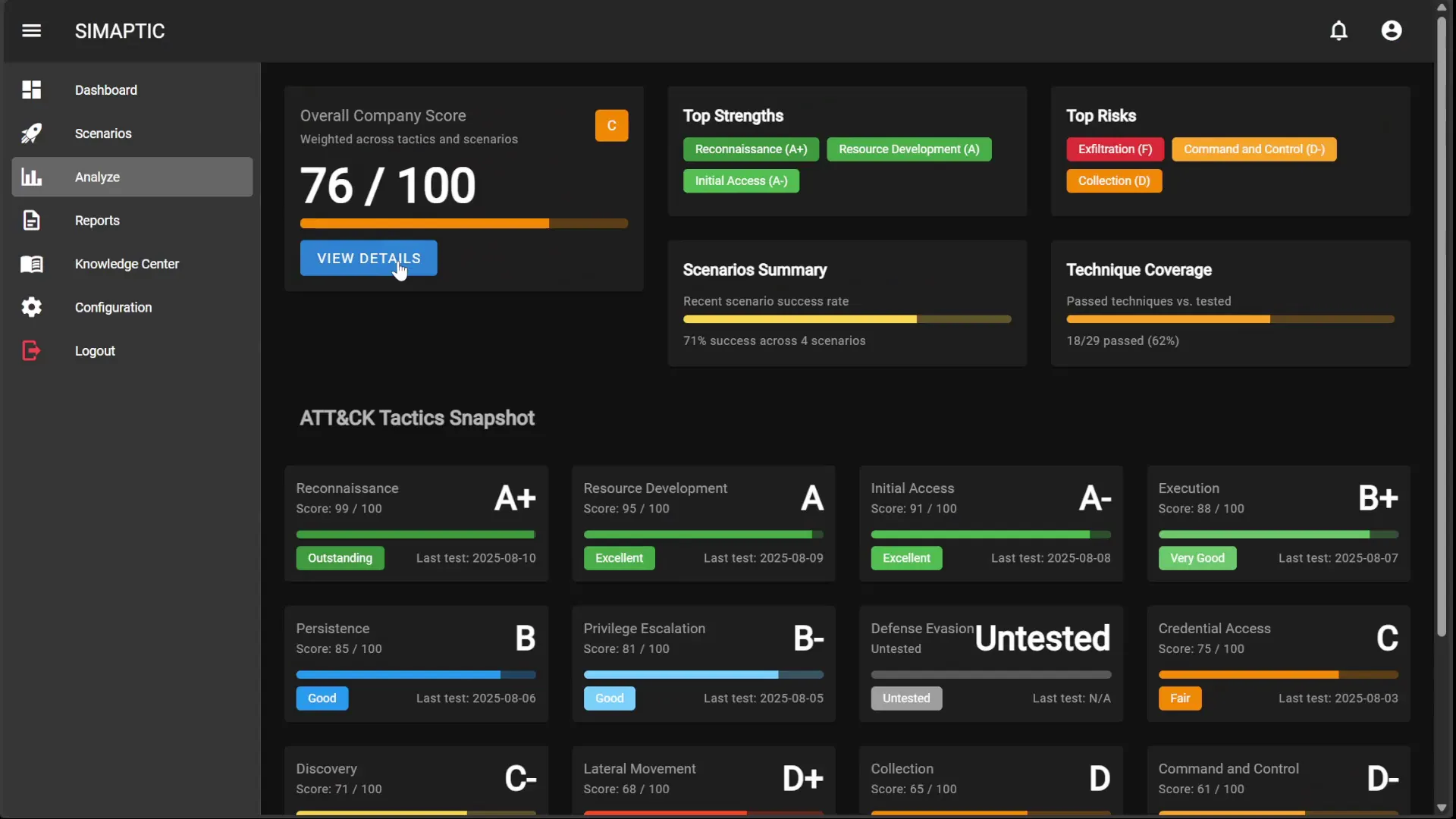
Built on Experience & Open Innovation
SIMAPTIC is built by veterans of offense and defense, incorporating lessons from elite red-team frameworks and open-source projects. We rapidly integrate community research and threat intelligence to emulate emerging attacker patterns.
Why Traditional Simulations Fall Short?
Many exercises assume predictable attackers and generate synthetic activity instead of real attack signals, creating a false sense of security. Common gaps include infrequent, point-in-time tests, fake behavior that doesn’t run real code or command-and-control, narrow scenarios, and minimal continuous feedback.
Choosing SIMAPTIC
- Trust in Realism: See the exact IOCs your environment would generate.
- Leverage Expertise: Decades of practical cyber experience baked in.
- Future-Proof Testing: On-premises, cloud, and hybrid, including realistic C2.
- Peace of Mind: As attacks rise year over year, let SIMAPTIC be your automated front line.
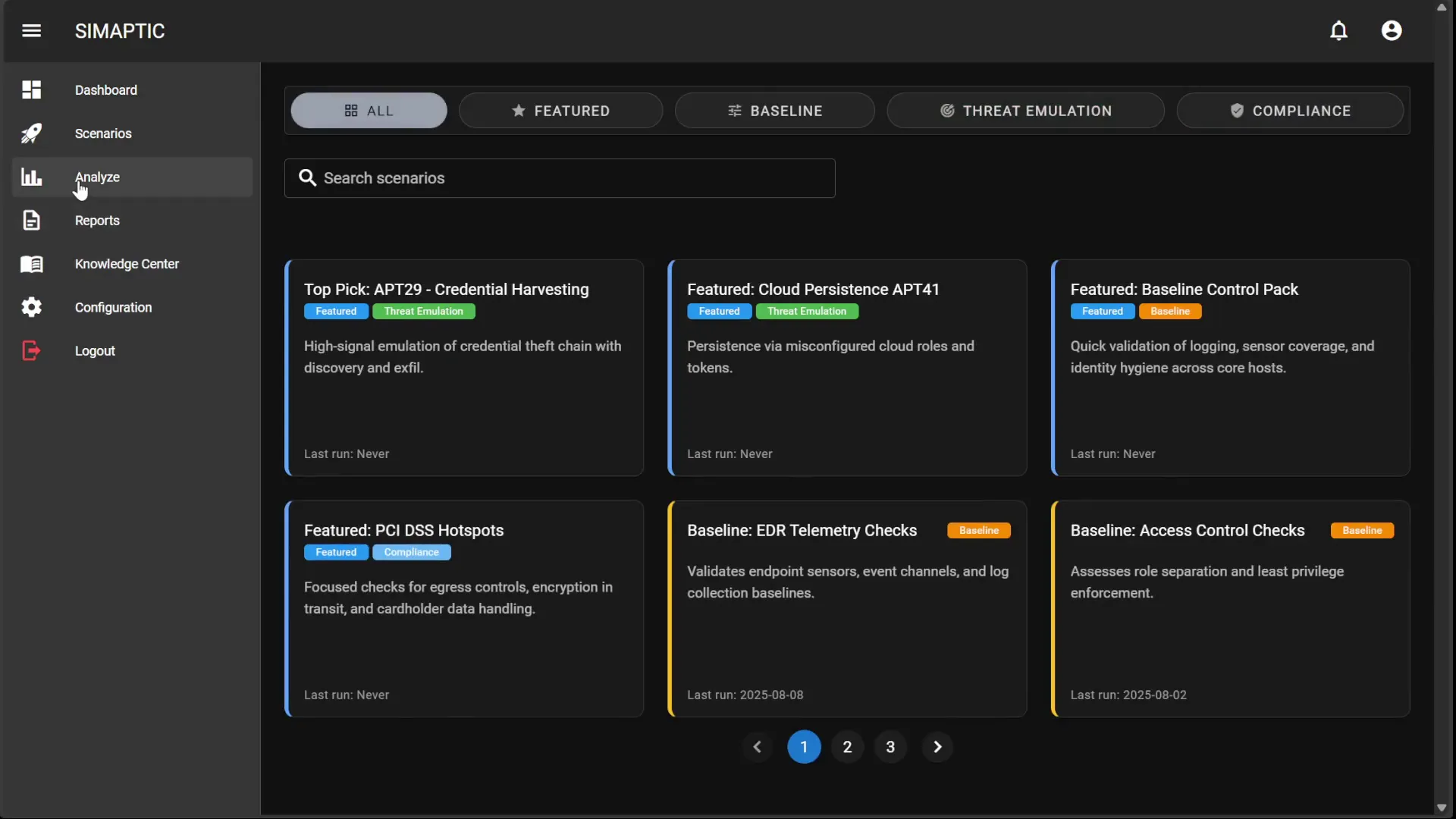
Frequently Asked Questions
SIMAPTIC uses agentic AI to plan, execute, and report realistic multi-stage campaigns (credentials → lateral movement → exfiltration). Unlike tools that “mock” behavior, SIMAPTIC can emit real indicators and controlled C2 traffic (opt-in) to validate detections end-to-end. Reports map to MITRE ATT&CK, surface missed detections, and recommend fixes.